I did create a few Dynamic Distribution Lists (DDLs) for a customer today. His request was to filter out disabled accounts.
If you google it, you will find something like this everywhere:
-not(userAccountControl -eq 'AccountDisabled, NormalAccount')Code language: JavaScript (javascript)For some reason this was not working for me, even if I tried a few variations of this “switch”.
So I took a look on Microsoft documentation about DDLs (I was looking for -RecipientFilter option).
It’s explained what it is on a Microsoft website, but in this case the important part is:
Property is a filterable property. For filterable properties, see Filterable properties for the RecipientFilter parameter.
So, on that “Filterable properties..” website I searched for: UserAccountControl,
where the value of this property is:
For valid values, see the Remarks section in User-Account-Control attribute. You need to convert the hexadecimal values to decimal. Most of the text values won’t work as described (even if you remove ADS_UF and all underscores).
So, in order to get this working, I need to use a decimal value of UserAccountControl attribute from AD … right ? Right !
You can check the value in AD in Attributes of AD object (on some user account).
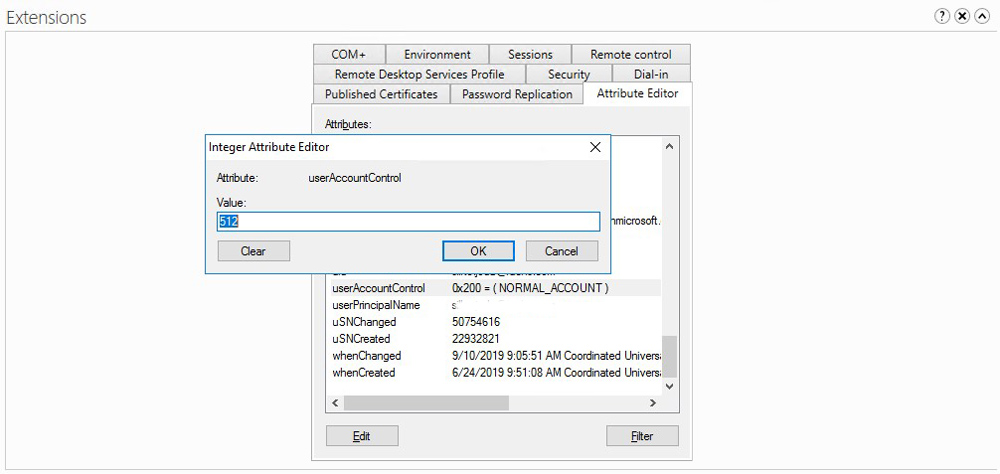
Possible values are:
| Property Flag | Hex value | Decimal value |
|---|---|---|
| NORMAL_ACCOUNT | 0x0200 | 512 |
| Disabled Account | 0x0202 | 514 |
| Enabled, Password Not Required | 0x0220 | 544 |
| Disabled, Password Not Required | 0x0222 | 546 |
| Enabled, Password Doesn’t Expire | 0x10200 | 66048 |
| Disabled, Password Doesn’t Expire | 0x10202 | 66050 |
| Disabled, Password Doesn’t Expire & Not Required | 0x10222 | 66082 |
All possible values for UserAccountControl:
| Property Flag | Hex value | Decimal value |
|---|---|---|
| SCRIPT | 0x0001 | 1 |
| ACCOUNTDISABLE | 0x0002 | 2 |
| HOMEDIR_REQUIRED | 0x0008 | 8 |
| LOCKOUT | 0x0010 | 16 |
| PASSWD_NOTREQD | 0x0020 | 32 |
| PASSWD_CANT_CHANGE | 0x0040 | 64 |
| ENCRYPTED_TEXT_PWD_ALLOWED | 0x0080 | 128 |
| TEMP_DUPLICATE_ACCOUNT | 0x0100 | 256 |
| NORMAL_ACCOUNT | 0x0200 | 512 |
| Disabled Account | 0x0202 | 514 |
| Enabled, Password Not Required | 0x0220 | 544 |
| Disabled, Password Not Required | 0x0222 | 546 |
| INTERDOMAIN_TRUST_ACCOUNT | 0x0800 | 2048 |
| WORKSTATION_TRUST_ACCOUNT | 0x1000 | 4096 |
| SERVER_TRUST_ACCOUNT | 0x2000 | 8192 |
| DONT_EXPIRE_PASSWORD | 0x10000 | 65536 |
| Enabled, Password Doesn’t Expire | 0x10200 | 66048 |
| Disabled, Password Doesn’t Expire | 0x10202 | 66050 |
| Disabled, Password Doesn’t Expire & Not Required | 0x10222 | 66082 |
| MNS_LOGON_ACCOUNT | 0x20000 | 131072 |
| SMARTCARD_REQUIRED | 0x40000 | 262144 |
| Enabled, Smartcard Required | 0x40200 | 262656 |
| Disabled, Smartcard Required | 0x40202 | 262658 |
| Disabled, Smartcard Required, Password Not Required | 0x40222 | 262690 |
| Disabled, Smartcard Required, Password Doesn’t Expire | 0x50202 | 328194 |
| Disabled, Smartcard Required, Password Doesn’t Expire & Not Required | 0x50222 | 328226 |
| TRUSTED_FOR_DELEGATION | 0x80000 | 524288 |
| Domain controller | 0x82000 | 532480 |
| NOT_DELEGATED | 0x100000 | 1048576 |
| USE_DES_KEY_ONLY | 0x200000 | 2097152 |
| DONT_REQ_PREAUTH | 0x400000 | 4194304 |
| PASSWORD_EXPIRED | 0x800000 | 8388608 |
| TRUSTED_TO_AUTH_FOR_DELEGATION | 0x1000000 | 16777216 |
| PARTIAL_SECRETS_ACCOUNT | 0x04000000 | 67108864 |
Property flag descriptions
- SCRIPT – The logon script will be run.
- ACCOUNTDISABLE – The user account is disabled.
- HOMEDIR_REQUIRED – The home folder is required.
- PASSWD_NOTREQD – No password is required.
- PASSWD_CANT_CHANGE – The user cannot change the password. This is a permission on the user’s object. For information about how to programmatically set this permission, visit the following Web site:http://msdn2.microsoft.com/en-us/library/aa746398.aspx
- ENCRYPTED_TEXT_PASSWORD_ALLOWED – The user can send an encrypted password.
- TEMP_DUPLICATE_ACCOUNT – This is an account for users whose primary account is in another domain. This account provides user access to this domain, but not to any domain that trusts this domain. This is sometimes referred to as a local user account.
- NORMAL_ACCOUNT – This is a default account type that represents a typical user.
- INTERDOMAIN_TRUST_ACCOUNT – This is a permit to trust an account for a system domain that trusts other domains.
- WORKSTATION_TRUST_ACCOUNT – This is a computer account for a computer that is running Microsoft Windows NT 4.0 Workstation, Microsoft Windows NT 4.0 Server, Microsoft Windows 2000 Professional, or Windows 2000 Server and is a member of this domain.
- SERVER_TRUST_ACCOUNT – This is a computer account for a domain controller that is a member of this domain.
- DONT_EXPIRE_PASSWD – Represents the password, which should never expire on the account.
- MNS_LOGON_ACCOUNT – This is an MNS logon account.
- SMARTCARD_REQUIRED – When this flag is set, it forces the user to log on by using a smart card.
- TRUSTED_FOR_DELEGATION – When this flag is set, the service account (the user or computer account) under which a service runs is trusted for Kerberos delegation. Any such service can impersonate a client requesting the service. To enable a service for Kerberos delegation, you must set this flag on the userAccountControl property of the service account.
- NOT_DELEGATED – When this flag is set, the security context of the user is not delegated to a service even if the service account is set as trusted for Kerberos delegation.
- USE_DES_KEY_ONLY – (Windows 2000/Windows Server 2003) Restrict this principal to use only Data Encryption Standard (DES) encryption types for keys.
- DONT_REQUIRE_PREAUTH – (Windows 2000/Windows Server 2003) This account does not require Kerberos pre-authentication for logging on.
- PASSWORD_EXPIRED – (Windows 2000/Windows Server 2003) The user’s password has expired.
- TRUSTED_TO_AUTH_FOR_DELEGATION – (Windows 2000/Windows Server 2003) The account is enabled for delegation. This is a security-sensitive setting. Accounts that have this option enabled should be tightly controlled. This setting lets a service that runs under the account assume a client’s identity and authenticate as that user to other remote servers on the network.
- PARTIAL_SECRETS_ACCOUNT – (Windows Server 2008/Windows Server 2008 R2) The account is a read-only domain controller (RODC). This is a security-sensitive setting. Removing this setting from an RODC compromises security on that server.
So as we have that information, the final “switch” will looks like this:
(UserAccountControl -eq '512') -or (UserAccountControl -eq '544') -or (UserAccountControl -eq '66048')Code language: JavaScript (javascript)
And whole basic cmdlet:
Set-DynamicDistributionGroup -identity “<Group Name>” -RecipientFilter {((Company -eq ‘NAME’) -and (RecipientType -eq ‘UserMailbox’) -and ((UserAccountControl -eq ‘512’) -or (UserAccountControl -eq ‘544’) -or (UserAccountControl -eq ‘66048’)))}
Note:
I include only enabled account in this “switch”. I do not exclude disabled accounts with ” -not ” switch, that’s because I tried that and it wasn’t working for me.

1 comment
J B
Thank you so much!