First step is to logon to the Azure portal > Azure AD > App registration and click on New registration.
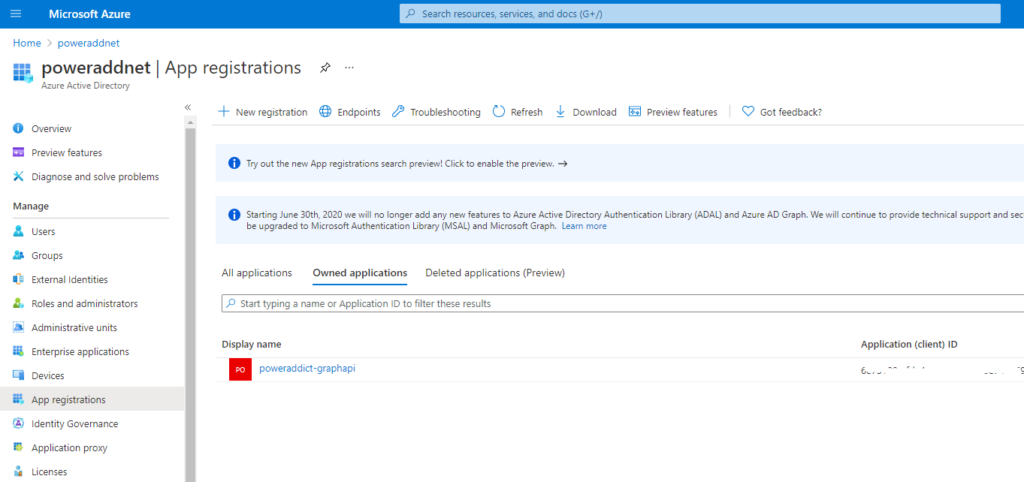
Next step is to configure API permissions you need (Add a permission) and if needed Grant admin consent.
A client application gains access to a resource server by declaring permission requests. Two types are available:
- “Delegated” permissions, which specify scope-based access using delegated authorization from the signed-in resource owner, are presented to the resource at run-time as “scp” claims in the client’s access token.
- “Application” permissions, which specify role-based access using the client application’s credentials/identity, are presented to the resource at run-time as “roles” claims in the client’s access token.
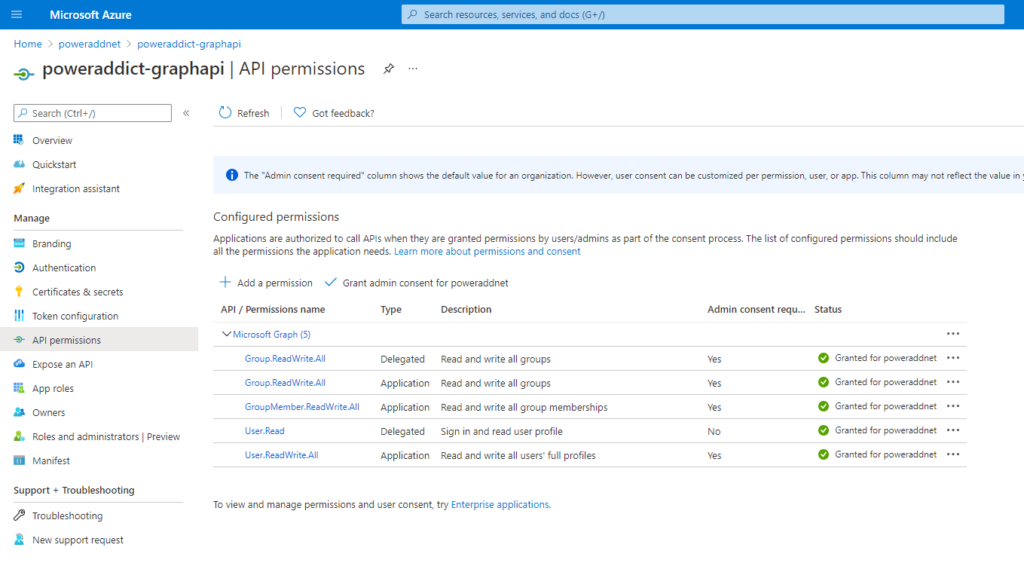
Next step is to create Client Secret.
Now the script to connect to MS Graph API and to get the token.
$ApplicationID = "APPLICATION (client) ID"
$TenatDomainName = "TENANT.onmicrosoft.com"
$AccessSecret = Read-Host "Enter Secret"
$Body = @{
Grant_Type = "client_credentials"
Scope = "https://graph.microsoft.com/.default"
client_Id = $ApplicationID
Client_Secret = $AccessSecret
}
$ConnectGraph = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$TenatDomainName/oauth2/v2.0/token" `
-Method POST -Body $Body
$token = $ConnectGraph.access_token
if ($null -eq $token)
{}
else {
Write-Host "Connected to MS Graph API" -ForegroundColor Green
}

1 comment
Max G.
Sir, I fucking LOVE you!
Thanks it worked beautifully